Fail2Ban is a must-have tool for safeguarding servers from brute-force attacks by blocking suspicious IPs automatically. In this detailed guide, we’ll walk you through every step to install, configure, and optimize Fail2Ban for automatic restarts in case of failure. Learn how to effectively enhance your VPS security with seamless IP blocking, ensuring continuous protection for your server. With clear instructions and practical tips, this guide ensures your website remains secure the right way. Stay ahead of potential threats and protect your online presence with Fail2Ban.
1. Install Fail2Ban
To get started, update your package manager and install Fail2Ban:
sudo apt update
sudo apt install fail2ban
2. Set Up Default Configuration
Make a copy of the default configuration file to avoid losing changes during updates:
sudo cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.local
Edit the copied file to enable SSH protection:
sudo nano /etc/fail2ban/jail.local
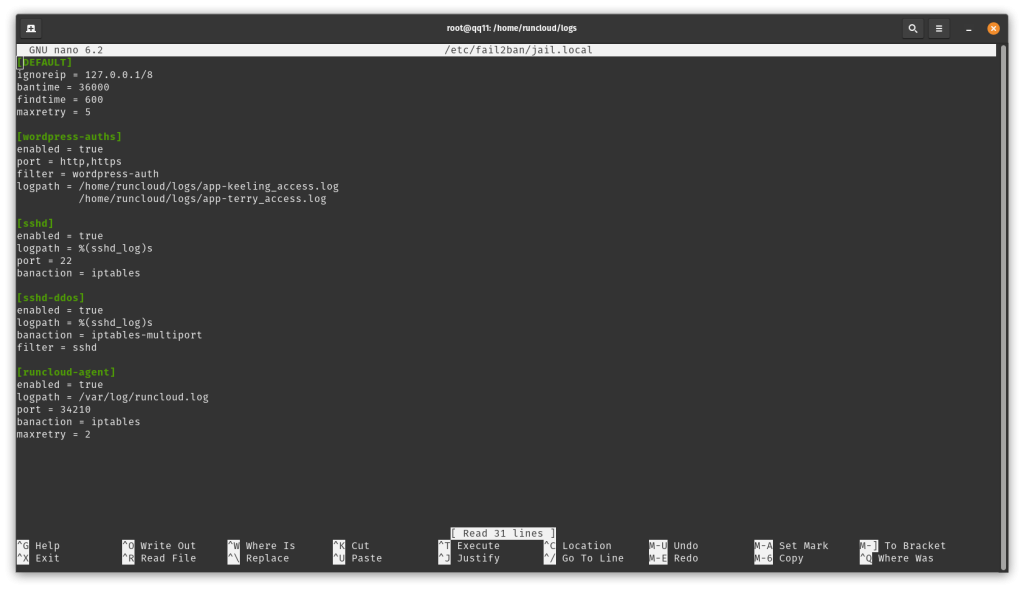
Update the [sshd] section as follows:
[sshd]
enabled = true
port = ssh
logpath = %(sshd_log)s
backend = systemd
3. Enable Fail2Ban on Boot
Ensure Fail2Ban starts with your server:
sudo systemctl enable fail2ban
Start and check its status:
sudo systemctl start fail2ban
sudo systemctl status fail2ban
4. Configure Automatic Restart
Prevent Fail2Ban from staying down in case of failure. Create an override file:
sudo mkdir -p /etc/systemd/system/fail2ban.service.d/
sudo nano /etc/systemd/system/fail2ban.service.d/override.conf
Add the following lines to enable auto-restart:
[Service]
Restart=always
RestartSec=5
Reload systemd and restart Fail2Ban:
sudo systemctl daemon-reload
sudo systemctl restart fail2ban
5. Verify Configuration Fail2ban
To check active jails and their statuses:
sudo fail2ban-client status
For detailed information about the SSH jail:
sudo fail2ban-client status sshd
With these steps, your server will be protected against brute force attacks and Fail2Ban will be set to automatically restart if it fails.
Related Questions
How can I fix the configuration error in /etc/fail2ban/jail.local
What should I do if the Fail2ban service does not start correctly
How can I check the Fail2ban logs for errors
What does error code 255/EXCEPTION mean in Fail2ban
How can I restart the Fail2ban service without errors



